MobSF is an automated security analysis tool designed for Mobile applications. It is compatible with Android, IOS, and Windows platforms. MobSF is a GUI based interface & dashboard panel that will make our analysis easy & more understandable. It supports mobile app binaries like apk, xapk, ipa & appx along with zipped source code also. MobSF framework could perform penetrating, malware analysis & security assessments for mobile platform applications. We can perform static & dynamic analysis. Its open source tool and MobSF community are updating the security updates as per the trending security flaws.
How to Install in Linux ?
In this blog we are using kali-linux 2021.3 Distro to make sure the distro is up to date. Firstly Download the file & just follow the command.
Git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
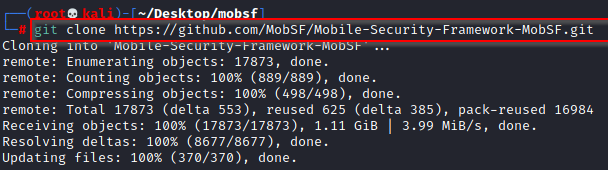
After installation Go to “Mobile-Security-Framework-MobSF” folder and following the below step
./setup.sh

Now, its Getting error for dependencies, So we should install dependency that shows in installation error.
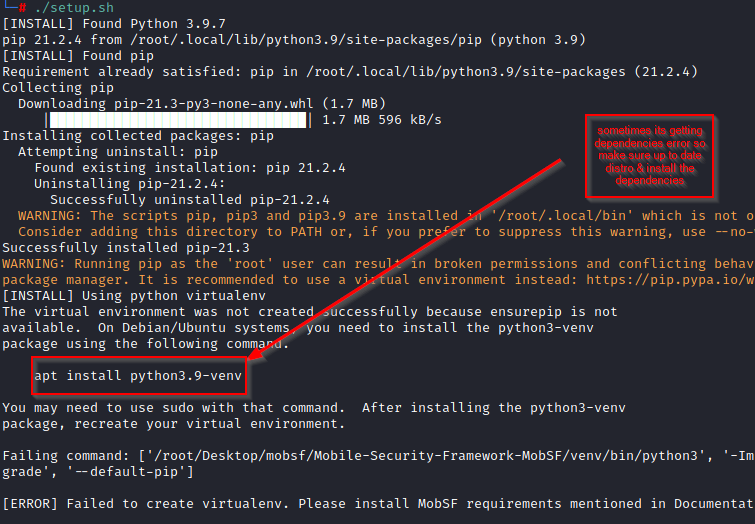
For installing the dependencies just follow the command. In this scenario it’s getting a “python3.9-venv” library error but in your situations it could be differ so check out the dependencies and then fix it. Now rerun the setup.
apt install python3.9-venv
./setup.sh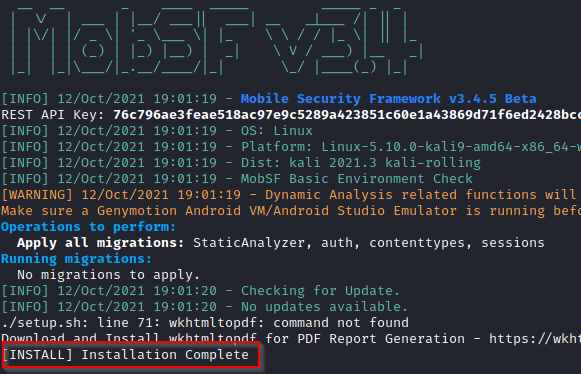
Now, all dependencies have installed. Now it’s time to run the mobSF framework.
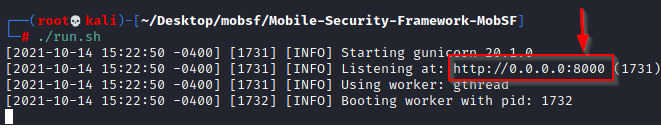
./run.sh

Accessing mobSF framework & Analyse the application.
For running the mobSF framework, just enter the url “http://localhost:8000” into the browser. You can check out the listening port when you run the script as shown in the image.
Now, the mobSF framework is ready to analyse the mobile application. Just drag and drop the application which you want to analyse. In this article we took android apk, and dragged into the mobSF framework and started to analyse the application. It takes some time to analyze the application. So Keep patience ! Until it’s completed.

After completing the application analysing. mobSF dashboard is opened and it shows the “static analyser” report. It collaborates the information in the tab, each tab has hold juicy information about the application. In the “APP SCORES” section they scored the application basis on Average CVSS, Security & trackers detection. On the “FILE INFORMATION” its shows the file name, size of application & hashes that they have used in application. You can see there are lots of tab and each tab has collaborate different information. lets find out each tab information.
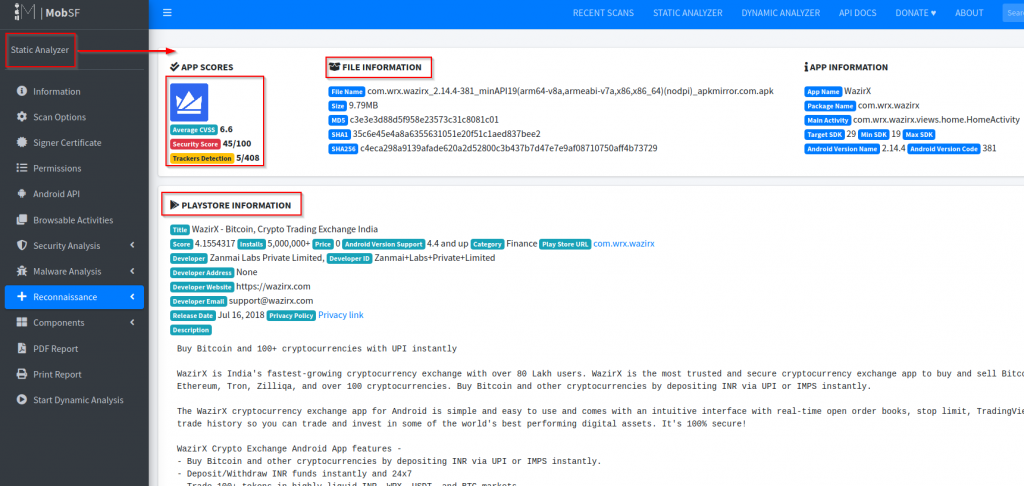
Information – it display application information i.e. app icon, app scores, application hashes, play store information – release date, application version, activity, services, receivers, providers, android support version and much more information just check out it
Scan options – It provides to re-scan the application & you can also start Dynamic Analysis, on the other hand You can view MANIFEST file, source code, you can also download the java code, smali code & apk file also.
Signer Certificate – It provides information about signature certificates & algorithms.
Application Permissions – it is showing the application permissions that the application uses when it’s running.
Android API – You can check out the api’s information
Browsable Activity – Browsable Activities that can be safely invoked from a browser. For example, if the user is viewing a web page or an e-mail and clicks on a link in the text, the Intent generated execute that link will require the BROWSABLE category, So that only activities supporting this category will be considered as possible actions.
Security Analysis – As the name it analysed the security flaws.
- Network Security – it analysed the network security that would be used into the application
- Manifest Analysis – In this section mobsf analysis the manifest file digs out the issues according to his severity impact.
- Code Analysis – It analyzes the code i.e java code and digs out the issues on the application and lists the list according to the impact of the issue.
- Binary Analysis – It shows analysis library binaries.
- NIAP Analysis – It ensures the security applications that have been implemented on it according to the government security policies.
- File Analysis – it shows the result of an analysed mobile application.
Malware Analysis – It analyses the malware on application here it is categorized the malware analysis in four different sections APKiD, Quark, Server locations & Domain malware check.
Reconnaissance – Here you can find out firebase url, email accounts, trackers – name, categories and urls, possible strings and last one is “Possible Hardcoded secrets” – into this you can find out active session management, firebase url, password, additional 2FA and much more dig into dive.
Components – In this section it is show Activities, Services, Receivers, Providers, all the possible libraries that could be used into it & into files options shows all the possible file like “assets/original.bin”, “firebase-components.properties” you can check out lots of file are there.
PDF Report – You can get download the report in pdf format
Print Report – You will prepare your report into a hard copy.